Wednesday, December 18, 2019
Monday, December 9, 2019
Tuesday, November 26, 2019
Tuesday, October 15, 2019
CYBER THREATS AND SECURITY
ONLINE THREATS (VIRUS, WORMS AND OTHER THREATS)
CYBER ATTACKS AND SECURITY
INTERNET SECURITY
Monday, October 14, 2019
Friday, October 11, 2019
SESSION 7 & 8 : ONLINE TRANSACTION & NETWORK/INTERNET SECURITY
ONLINE TRANSACTION
Online shopping is a form of electronic commerce where customers can buy or sell goods overthe Internet. Customers need to have an active internet connection for viewing goods or services
offered by a seller; customers can pay online using a credit, debit card or by internet banking.
Online shopping could be useful in situations when:
• A customer does not have sufficient time to visit stores.
• Visiting a store is more expensive than purchasing a product online.
• A product or service that is not available in the local market is available online.
Some of the popular online transaction websites are:
• IRCTC, an online portal for booking flight and train tickets.
• Flipkart, an online shopping portal for buying consumer products.
• EBay, an online portal for buying and selling goods.
• Redbus, an online portal for booking bus tickets.
To perform an online transaction, all you need is a web browser and an active internet connection.
In some cases where purchasing is involved, you will need a valid credit card, debit card or online
banking support referred to as Net Banking Subscription. Some websites even allow COD (Cash
on delivery) where the users can pay once they receive the product or service.
Answer the following:
1. Explain the purpose of Online transactions.
2. List any five websites that allow online transactions.
3. List any three payment tools to use online transactions.
Activity:
1. Register with Junglee/ Flipkart/ Amazon, Yatra, IRCTC, Redbus and practice online
transactions.
NETWORK/INTERNET SECURITY
Internet security is a branch of computer security specifically related to the Internet, often
involving browser security but also network security. Its objective is to establish rules and
measures to use against attacks over the Internet. The Internet represents an insecure channel
for exchanging information leading to a high risk of intrusion or fraud, such as phishing.
Online threats such as Phishing, email spoofing, chat spoofing, etc. can increase the chances of users getting compromised.
Online Threats :
Phishing:
Phishing is a method used by cyber-criminals who want to come to one’s personal information. By sending fake emails or contacting people directly through scam websites crooks gain personal data. Login credentials, social security number, credit card number, bank account information are just some information interesting to the hackers.
Spoofing :
The word "spoof" means to hoax, trick, or deceive. Therefore, in the IT world, spoofing refers tricking or deceiving computer systems or other computer users. This is typically done by hiding one's identity or faking the identity of another user on the Internet
Chating Spoofing :
When a computer system or a user of a computer masquerades to be another identity while engaging in chat is known as chat spoofing. Spoofing by definition means to trick or deceive someone. These kind of attacks are possible in cases where security is vulnerable in electronic communication. Spoofing attacks are usually targeted to get personal details of an individual like passwords, bank details, etc. so that it can be used illegitimately.
Email Spoofing :-
e-mail spoofing involves sending messages from a bogus e-mail address or faking the e-mail address of another user. Fortunately, most e-mail servers have security features that prevent unauthorized users from sending messages. However, spammers often send spam messages from their own SMTP, which allows them to use fake e-mail addresses. Therefore, it is possible to receive e-mail from an address that is not the actual address of the person sending the message.
Spyware
Any type of malware that collects personal information, browsing history, and one’s surfing habits is considered a spyware. Its name comes from a great ability to hide. First of all, collected information is shared with the third parties and then it gets abused.
Adware
Most of the adware are safe and consist of annoying pop-ups showing on your computer and browser. Adware is a type of free software supported by advertisement. The danger of adware reflects in the possibility of one being tracked through websites he/she visits. In the worst case, his/her personal information could be gathered through adware.
You can reduce the risks by using best practices such as using Antivirus Software, Antispyware Software, Firewalls, strong passwords, etc. in addition to spreading awareness of the best practices.
Best Practices for Security:-
Use strong passwords, a combination of alphanumeric and special characters could be used
for creating a password that is not so easy to crack or guessed by other users.
Following is a general guideline for managing strong passwords.
• Keep the length of the password at least 12-14 characters if permitted.
• Avoid keeping passwords based on repetition, dictionary words, letter or number sequences,
usernames, relative or pet names, etc.
• Including numbers, and symbols in passwords if allowed.
• Use capital and lower-case letters.
• Avoid using the same password for multiple sites or purposes.
• Avoid using something that the public or workmates know you strongly like or dislike.
• Use random password generators if possible.
Example of a strong password: u1vX:,4Hd{]$
You may also use websites such as www.strongpasswordgenerator.com that can generate
random strong passwords.
Practice:-
• Open any web browser. Type www.strongpasswordgenerator.com in the address bar and
press Enter.
• Click Generate strong password. Notice the password displayed under your new password.
Backup your data: Always keep copies of personal data in additional media such as compact
discs, pen drives, etc.This could be helpful in situation when there is a loss of data.
from unauthorized users.
Keeping your username and password private: Never save your username or password on
computers that are used in shared environments such as internet café.
Registering with websites: Read the privacy statement or policy whenever you register with
a website, the statement or policy will include information about how the website use personal
data.
Do not share personal information: Websites require you to fill out forms containing fields
such as name, gender, age, email address, school, etc. Be cautious when filling out such
forms; research and verify if it’s a trustable website .
Secure transactions: If you are using online shopping or transactions, websites even store
your credit card or online banking personal information such as your credit card number, account
details, etc. This information can be tracked and used by un-authorized users often known as
hackers to misuse this information. Again, ensure the website is legitimate and uses secure
practices for performing and maintaining online transactions.
Use antivirus and antispyware software: Computers are prone to attacks from software known
as Malware that could harm your computer. Malware track browsing behavior or transmit personal data from your computer; programs such as keyloggers could be installed on your computer track and transmit every key that is pressed on a keyboard (keystrokes) to unauthorized users.
Antivirus and Antispyware programs also offer real-time protection monitoring your computer for
any changes by malware software. Keep your Antivirus and Antispyware software always up to
date, this can help in protecting your computer from recent threats.
Do not immediately respond to mails from unknown users: It may be a fake mail trying to
gather personal information such as your bank account details, home address, etc. Some mails
could promise you jobs or announce lottery results which in turn could compromise the user.
And in some cases, virus or scripts that are dangerous could be attached to the mail; NEVER
open the attachment from an unknown source.
Clear browser cookies frequently: Cookies are programs that are created on your local
computer when you visit websites. Though cookies are meant for storing data based on your
activity performed during your earlier visit such as logon details, details of a shopping cart,
visited pages in a website, etc.
Keep the operating system and software applications up to date.
Install firewalls: Firewalls could be software or hardware and can assist in keeping a computer
and a network secure. Firewalls analyze the network traffic and determine if the traffic should be
allowed or not. In most cases, operating systems such as Linux, Windows or Mac include firewall
software as a part of operating system thus keeping the computer secure.
Never install software from unknown sources: As they might not be trustworthy; download
only from well-known or reputed websites. Verify the source if it is legitimate by searching the
internet or referring to comments from other users before downloading them.
Remove unwanted or unknown software applications: These might have got installed without
your knowledge when you have visited some websites. Unwanted software could get installed as
they might have been bundled along with necessary software. Some programs such as toolbars
get installed usually through bundled software and are programmed to send personal data without
your consent.
Answer the following:
1. Explain the purpose of Internet Security.
2. Explain different kinds of online threats.
SESSION 5 & 6 (BLOG)
CREATING AND PUBLISHING WEBPAGES :- BLOG
BLOG:-
A blog is a discussion style site used by non-technical (or technical users) users for creating
personal web pages. Blogs are similar to an online personal diary and simple to use.
You can use a blog to convey messages about events, announcements, news, reviews, etc. Blogs are usually managed using a web browser and this requires active internet connection.
You can also use offline blog software to create content first and later publish the content when an active internet connection is available.
There are hundreds of websites that offer blog service for free. Some of the popular blogs include:
• www.WordPress.com
• www.blogger.com
• www.blog.com
• www.weebly.com
• www.blogsome.com
OFFLINE BLOG EDITORS :
An offline blog editor is an amazing tool for bloggers because it lets you create blog posts without an internet connection. So, instead of waiting to wait for an online editor to load and then worry that a hiccup in your network connection could cancel out all your work, you can just work offline.
Offline editors let you create, edit, and format your content before you upload it to your website. Then, if you have an internet connection, you can publish the posts directly to your blog.
Top Offline Blog Editors
- Windows Live Writer (Windows) Windows Live Writer is, as you might guess from its name, Windows-compatible, and owned by Microsoft. ...
- BlogDesk (Windows) BlogDesk is also free and can be used on Windows as your offline blog editor. ...
- Qumana (Windows & Mac) ...
- MarsEdit (Mac) ...
- Ecto (Mac) ...
- BlogJet (Windows) ...
- Bits (Mac) ...
- Blogo (Mac)
Perform the following activities till you are confident:
Activities
1. You have learnt to create and work with blogs using WordPress. Now create and work with other blog websites such as blogger, weebly,
2. Create blogs for:
• Announcing School Annual Day Function
• Blood Donation Camp
ASSESSMENT
Answer the following:
1. Explain the purpose of a blog.
2. List any 5 websites that provide blog service.
3. Difference between web page and website.
4. Explain the purpose of an offline blog editor.
5. List any five offline blog editors.
Thursday, October 10, 2019
AUTUMN BREAK HOMEWORK 2019-20
Autumn Break Home Work
Class – X
Subject: - IT (Information Technology)-402
Activity (For Practical Notebook):
1. Create a blog one of the following topic:-a. Annual Sports day ( also posts like when organize, where organize, which sports activity and photos)
b. Blood Donation Camp
Write down the steps with diagram.
2. Register with shopping site (flipkart, junglee, amazon etc) or travelling site (IRCTC, Yatra, RedBus etc.) and perform how to perform online transaction. Write down the steps with diagrams.
3. How to Clearing data stored in browsers Do this activity one of following browser :-
a. Mozilla Firefox
b. Google Chrome
c. Internet Explorer
Write steps with diagrams.
For I.T. Theory Notebook:-
1. List any five offline blog editors.2. Explain the purpose of an offline blog editor.
3. Explain the purpose of online transaction.
4. List any five websites that allow online transaction.
5. List any three payment tools to use online transaction.
6. Explain the purpose of Internet Security and also define the different kinds of online threats.
Thursday, September 12, 2019
Tuesday, September 3, 2019
Monday, February 25, 2019
E-mail Providers
E-Mail Providers
There are several email service providers available in the market with their enabled features such as sending, receiving, drafting, storing an email and much more.
The following table shows the popular email service providers:
| S.N. | Service and Description |
|---|---|
| 1. | Gmail Gmail is an email service that allows users to collect all the messages. It also offers approx 7 GB of free storage. |
| 2. | Hotmail Hotmail offers free email and practically unlimited storage accessible on web. |
| 3. | Yahoo Mail Yahoo Mail offers unlimited storage, SMS texting, social networking and instant messaging to boot. |
| 4. | iCloud Mail iCloud Mail offers ample storage, IMAP access, and an elegantly functional web application. |
| 5. | ATM Mail ATM Mail is a free email service with good spam protection. |
| 6. | Mail.com and GMX Mail Mail.com and GMX Mail offers reliable mail service with unlimited online storage. |
| 7. | Shortmail Shortmail offers easy and fast email service but with limited 500 characters per message. |
| 8. | Inbox.com Inbox.com offers 5 GB of free online storage. IMAP is not supported by Inbox.com |
| 9. | Facebook Messages Facebook Messages includes the message conversation. |
| 10. | My Way Mail My Way Mail offers clean and fast free email service but lacks in secure messaging. |
E-Mail Security
E-Mail Security
E-mail Hacking
Email hacking can be done in any of the following ways:
- Spam
- Virus
- Phishing
Spam
E-mail spamming is an act of sending Unsolicited Bulk E-mails (UBI) which one has not asked for. Email spams are the junk mails sent by commercial companies as an advertisement of their products and services.
Virus
Some emails may incorporate with files containing malicious script which when run on your computer may lead to destroy your important data.
Phishing
Email phishing is an activity of sending emails to a user claiming to be a legitimate enterprise. Its main purpose is to steal sensitive information such as usernames, passwords, and credit card details.
Such emails contains link to websites that are infected with malware and direct the user to enter details at a fake website whose look and feels are same to legitimate one.
E-mail Spamming and Junk Mails
Email spamming is an act of sending Unsolicited Bulk E-mails (UBI) which one has not asked for. Email spams are the junk mails sent by commercial companies as an advertisement of their products and services.
Spams may cause the following problems:
- It floods your e-mail account with unwanted e-mails, which may result in loss of important e-mails if inbox is full.
- Time and energy is wasted in reviewing and deleting junk emails or spams.
- It consumes the bandwidth that slows the speed with which mails are delivered.
- Some unsolicited email may contain virus that can cause harm to your computer.
Blocking Spams
Following ways will help you to reduce spams:
- While posting letters to newsgroups or mailing list, use a separate e-mail address than the one you used for your personal e-mails.
- Don’t give your email address on the websites as it can easily be spammed.
- Avoid replying to emails which you have received from unknown persons.
- Never buy anything in response to a spam that advertises a product.
E-mail Cleanup and Archiving
In order to have light weighted Inbox, it’s good to archive your inbox from time to time. Here I will discuss the steps to clean up and archive your Outlook inbox.
- Select File tab on the mail pane.
- Select Cleanup Tools button on account information screen.
- Select Archive from cleanup tools drop down menu.
- Select Archive this folder and all subfolders option and then click on the folder that you want to archive. Select the date from the Archive items older than: list. Click Browse to create new .pst file name and location. Click OK.
E-mail Operation & Creation
Creating Email Account
There are various email service provider available such as Gmail, hotmail, ymail, rediff mail etc. Here we will learn how to create an account using Gmail.
- Open gmail.com and click create an account.
- Now a form will appear. Fill your details here and click Next Step.
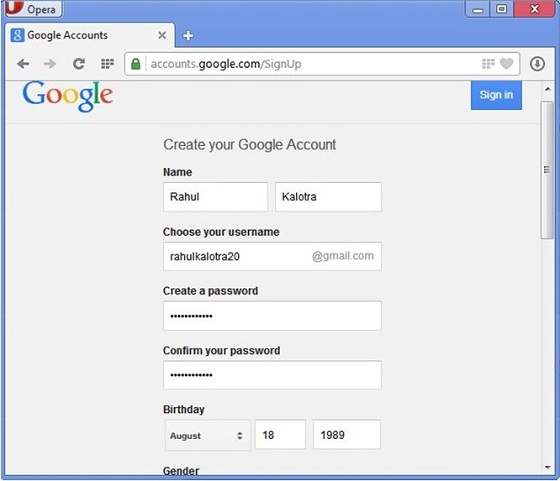
- This step allows you to add your picture. If you don’t want to upload now, you can do it later. Click Next Step.
- Now a welcome window appears. Click Continue to Gmail.
- Wow!! You are done with creating your email account with Gmail. It’s that easy. Isn’t it?
- Now you will see your Gmail account as shown in the following image:
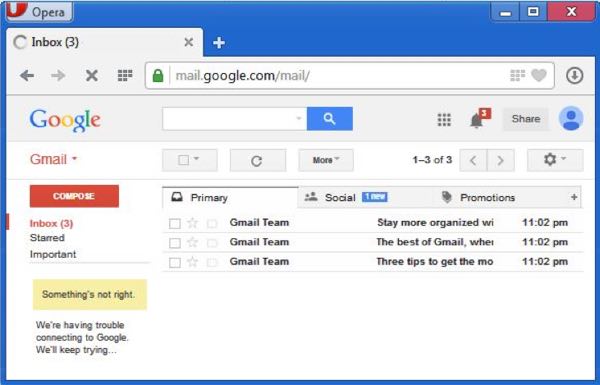
Key Points:
- Gmail manages the mail into three categories namely Primary, Socialand Promotions.
- Compose option is given at the right to compose an email message.
- Inbox, Starred, Sent mail, Drafts options are available on the left pane which allows you to keep track of your emails.
Composing and Sending Email
Before sending an email, we need to compose a message. When we are composing an email message, we specify the following things:
- Sender’s address in To field
- Cc (if required)
- Bcc (if required)
- Subject of email message
- Text
- Signature
You should specify the correct email address; otherwise it will send an error back to the sender.
Once you have specified all the above parameters, It’s time to send the email. The mailer program provides a Send button to send email, when you click Send, it is sent to the mail server and a message mail sent successfully is shown at the above.
Reading Email
Every email program offers you an interface to access email messages. Like in Gmail, emails are stored under different tabs such as primary, social, and promotion. When you click one of tab, it displays a list of emails under that tab.
In order to read an email, you just have to click on that email. Once you click a particular email, it gets opened.
The opened email may have some file attached with it. The attachments are shown at the bottom of the opened email with an option called download attachment.
Replying Email
After reading an email, you may have to reply that email. To reply an email, click Reply option shown at the bottom of the opened email.
Once you click on Reply, it will automatically copy the sender’s address in to the To field. Below the To field, there is a text box where you can type the message.
Once you are done with entering message, click Send button. It’s that easy. Your email is sent.
Forwarding Email
It is also possible to send a copy of the message that you have received along with your own comments if you want. This can be done using forward button available in mail client software.
The difference between replying and forwarding an email is that when you reply a message to a person who has send the mail but while forwarding you can send it to anyone.
When you receive a forwarded message, the message is marked with a > character in front of each line and Subject: field is prefixed with Fw.
Deleting Email
If you don’t want to keep email into your inbox, you can delete it by simply selecting the message from the message list and clicking delete or pressing the appropriate command.
Some mail clients offers the deleted mails to be stored in a folder called deleted items or trash from where you can recover a deleted email.
Subscribe to:
Comments (Atom)








































