E-Mail Working Process
Monday, February 25, 2019
E-mail Providers
E-Mail Providers
There are several email service providers available in the market with their enabled features such as sending, receiving, drafting, storing an email and much more.
The following table shows the popular email service providers:
| S.N. | Service and Description |
|---|---|
| 1. | Gmail Gmail is an email service that allows users to collect all the messages. It also offers approx 7 GB of free storage. |
| 2. | Hotmail Hotmail offers free email and practically unlimited storage accessible on web. |
| 3. | Yahoo Mail Yahoo Mail offers unlimited storage, SMS texting, social networking and instant messaging to boot. |
| 4. | iCloud Mail iCloud Mail offers ample storage, IMAP access, and an elegantly functional web application. |
| 5. | ATM Mail ATM Mail is a free email service with good spam protection. |
| 6. | Mail.com and GMX Mail Mail.com and GMX Mail offers reliable mail service with unlimited online storage. |
| 7. | Shortmail Shortmail offers easy and fast email service but with limited 500 characters per message. |
| 8. | Inbox.com Inbox.com offers 5 GB of free online storage. IMAP is not supported by Inbox.com |
| 9. | Facebook Messages Facebook Messages includes the message conversation. |
| 10. | My Way Mail My Way Mail offers clean and fast free email service but lacks in secure messaging. |
E-Mail Security
E-Mail Security
E-mail Hacking
Email hacking can be done in any of the following ways:
- Spam
- Virus
- Phishing
Spam
E-mail spamming is an act of sending Unsolicited Bulk E-mails (UBI) which one has not asked for. Email spams are the junk mails sent by commercial companies as an advertisement of their products and services.
Virus
Some emails may incorporate with files containing malicious script which when run on your computer may lead to destroy your important data.
Phishing
Email phishing is an activity of sending emails to a user claiming to be a legitimate enterprise. Its main purpose is to steal sensitive information such as usernames, passwords, and credit card details.
Such emails contains link to websites that are infected with malware and direct the user to enter details at a fake website whose look and feels are same to legitimate one.
E-mail Spamming and Junk Mails
Email spamming is an act of sending Unsolicited Bulk E-mails (UBI) which one has not asked for. Email spams are the junk mails sent by commercial companies as an advertisement of their products and services.
Spams may cause the following problems:
- It floods your e-mail account with unwanted e-mails, which may result in loss of important e-mails if inbox is full.
- Time and energy is wasted in reviewing and deleting junk emails or spams.
- It consumes the bandwidth that slows the speed with which mails are delivered.
- Some unsolicited email may contain virus that can cause harm to your computer.
Blocking Spams
Following ways will help you to reduce spams:
- While posting letters to newsgroups or mailing list, use a separate e-mail address than the one you used for your personal e-mails.
- Don’t give your email address on the websites as it can easily be spammed.
- Avoid replying to emails which you have received from unknown persons.
- Never buy anything in response to a spam that advertises a product.
E-mail Cleanup and Archiving
In order to have light weighted Inbox, it’s good to archive your inbox from time to time. Here I will discuss the steps to clean up and archive your Outlook inbox.
- Select File tab on the mail pane.
- Select Cleanup Tools button on account information screen.
- Select Archive from cleanup tools drop down menu.
- Select Archive this folder and all subfolders option and then click on the folder that you want to archive. Select the date from the Archive items older than: list. Click Browse to create new .pst file name and location. Click OK.
E-mail Operation & Creation
Creating Email Account
There are various email service provider available such as Gmail, hotmail, ymail, rediff mail etc. Here we will learn how to create an account using Gmail.
- Open gmail.com and click create an account.
- Now a form will appear. Fill your details here and click Next Step.
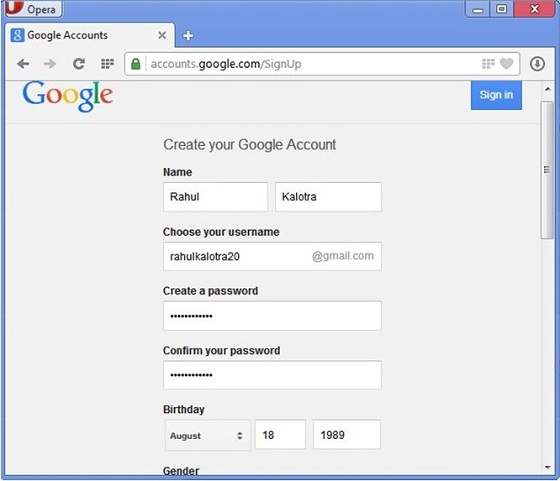
- This step allows you to add your picture. If you don’t want to upload now, you can do it later. Click Next Step.
- Now a welcome window appears. Click Continue to Gmail.
- Wow!! You are done with creating your email account with Gmail. It’s that easy. Isn’t it?
- Now you will see your Gmail account as shown in the following image:
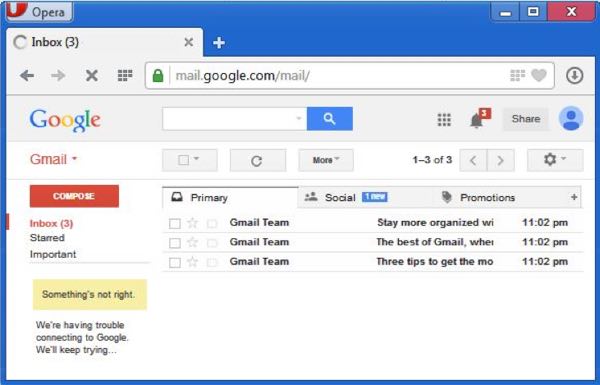
Key Points:
- Gmail manages the mail into three categories namely Primary, Socialand Promotions.
- Compose option is given at the right to compose an email message.
- Inbox, Starred, Sent mail, Drafts options are available on the left pane which allows you to keep track of your emails.
Composing and Sending Email
Before sending an email, we need to compose a message. When we are composing an email message, we specify the following things:
- Sender’s address in To field
- Cc (if required)
- Bcc (if required)
- Subject of email message
- Text
- Signature
You should specify the correct email address; otherwise it will send an error back to the sender.
Once you have specified all the above parameters, It’s time to send the email. The mailer program provides a Send button to send email, when you click Send, it is sent to the mail server and a message mail sent successfully is shown at the above.
Reading Email
Every email program offers you an interface to access email messages. Like in Gmail, emails are stored under different tabs such as primary, social, and promotion. When you click one of tab, it displays a list of emails under that tab.
In order to read an email, you just have to click on that email. Once you click a particular email, it gets opened.
The opened email may have some file attached with it. The attachments are shown at the bottom of the opened email with an option called download attachment.
Replying Email
After reading an email, you may have to reply that email. To reply an email, click Reply option shown at the bottom of the opened email.
Once you click on Reply, it will automatically copy the sender’s address in to the To field. Below the To field, there is a text box where you can type the message.
Once you are done with entering message, click Send button. It’s that easy. Your email is sent.
Forwarding Email
It is also possible to send a copy of the message that you have received along with your own comments if you want. This can be done using forward button available in mail client software.
The difference between replying and forwarding an email is that when you reply a message to a person who has send the mail but while forwarding you can send it to anyone.
When you receive a forwarded message, the message is marked with a > character in front of each line and Subject: field is prefixed with Fw.
Deleting Email
If you don’t want to keep email into your inbox, you can delete it by simply selecting the message from the message list and clicking delete or pressing the appropriate command.
Some mail clients offers the deleted mails to be stored in a folder called deleted items or trash from where you can recover a deleted email.
E-mail Working System
E-Mail Working System
E-mail System
E-mail system comprises of the following three components:
- Mailer
- Mail Server
- Mailbox
Mailer
It is also called mail program, mail application or mail client. It allows us to manage, read and compose e-mail.
Mail Server
The function of mail server is to receive, store and deliver the email. It is must for mail servers to be Running all the time because if it crashes or is down, email can be lost.
Mailboxes
Mailbox is generally a folder that contains emails and information about them.
Working of E-mail
Email working follows the client server approach. In this client is the mailer i.e. the mail application or mail program and server is a device that manages emails.
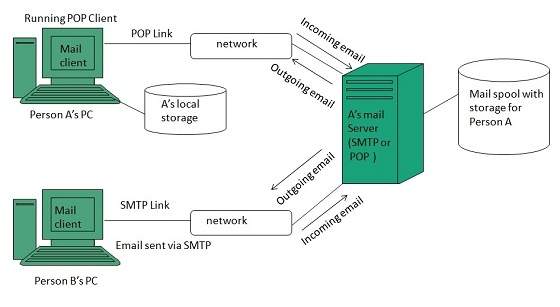
Following example will take you through the basic steps involved in sending and receiving emails and will give you a better understanding of working of email system:
- Suppose person A wants to send an email message to person B.
- Person A composes the messages using a mailer program i.e. mail client and then select Send option.
- The message is routed to Simple Mail Transfer Protocol to person B’s mail server.
- The mail server stores the email message on disk in an area designated for person B.
The disk space area on mail server is called mail spool.
- Now, suppose person B is running a POP client and knows how to communicate with B’s mail server.
- It will periodically poll the POP server to check if any new email has arrived for B.As in this case, person B has sent an email for person B, so email is forwarded over the network to B’s PC. This is message is now stored on person B’s PC.
The following diagram gives pictorial representation of the steps discussed above:
2.

E-mail Protocols
E-mail Protocols
E-mail Protocols are set of rules that help the client to properly transmit the information to or from the mail server. Here in this tutorial, we will discuss various protocols such as SMTP, POP, and IMAP.
SMTP
SMTP stands for Simple Mail Transfer Protocol. It was first proposed in 1982. It is a standard protocol used for sending e-mail efficiently and reliably over the internet.
Key Points:
- SMTP is application level protocol.
- SMTP is connection oriented protocol.
- SMTP is text based protocol.
- It handles exchange of messages between e-mail servers over TCP/IP network.
- Apart from transferring e-mail, SMPT also provides notification regarding incoming mail.
- When you send e-mail, your e-mail client sends it to your e-mail server which further contacts the recipient mail server using SMTP client.
- These SMTP commands specify the sender’s and receiver’s e-mail address, along with the message to be send.
- The exchange of commands between servers is carried out without intervention of any user.
- In case, message cannot be delivered, an error report is sent to the sender which makes SMTP a reliable protocol.
IMAP
IMAP stands for Internet Mail Access Protocol. It was first proposed in 1986. There exist five versions of IMAP as follows:
- Original IMAP
- IMAP2
- IMAP3
- IMAP2bis
- IMAP4
Key Points:
- IMAP allows the client program to manipulate the e-mail message on the server without downloading them on the local computer.
- The e-mail is hold and maintained by the remote server.
- It enables us to take any action such as downloading, delete the mail without reading the mail.It enables us to create, manipulate and delete remote message folders called mail boxes.
- IMAP enables the users to search the e-mails.
- It allows concurrent access to multiple mailboxes on multiple mail servers.
POP
POP stands for Post Office Protocol. It is generally used to support a single client. There are several versions of POP but the POP 3 is the current standard.
Key Points
- POP is an application layer internet standard protocol.
- Since POP supports offline access to the messages, thus requires less internet usage time.
- POP does not allow search facility.
- In order to access the messaged, it is necessary to download them.
- It allows only one mailbox to be created on server.
- It is not suitable for accessing non mail data.
- POP commands are generally abbreviated into codes of three or four letters. Eg. STAT.
Comparison between POP and IMAP
| S.N. | POP | IMAP |
|---|---|---|
| 1 | Generally used to support single client. | Designed to handle multiple clients. |
| 2 | Messages are accessed offline. | Messages are accessed online although it also supports offline mode. |
| 3 | POP does not allow search facility. | It offers ability to search emails. |
| 4 | All the messages have to be downloaded. | It allows selective transfer of messages to the client. |
| 5 | Only one mailbox can be created on the server. | Multiple mailboxes can be created on the server. |
| 6 | Not suitable for accessing non-mail data. | Suitable for accessing non-mail data i.e. attachment. |
| 7 | POP commands are generally abbreviated into codes of three or four letters. Eg. STAT. | IMAP commands are not abbreviated, they are full. Eg. STATUS. |
| 8 | It requires minimum use of server resources. | Clients are totally dependent on server. |
| 9 | Mails once downloaded cannot be accessed from some other location. | Allows mails to be accessed from multiple locations. |
| 10 | The e-mails are not downloaded automatically. | Users can view the headings and sender of e-mails and then decide to download. |
| 10 | POP requires less internet usage time. | IMAP requires more internet usage time. |
Learn About E-mail
Email is a service which allows us to send the message in electronic mode over the internet. It offers an efficient, inexpensive and real time mean of distributing information among people.
E-Mail Address
Each user of email is assigned a unique name for his email account. This name is known as E-mail address. Different users can send and receive messages according to the e-mail address.
E-mail is generally of the form username@domainname. For example, webmaster@tutorialspoint.com is an e-mail address where webmaster is username and tutorialspoint.com is domain name.
E-mail Message Components
E-mail message comprises of different components: E-mail Header, Greeting, Text, and Signature. These components are described in the following diagram:
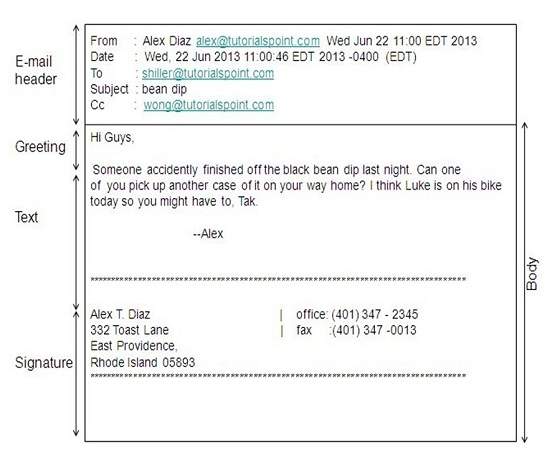
E-mail Header
The first five lines of an E-mail message is called E-mail header. The header part comprises of following fields:
- From
- Date
- To
- Subject
- CC
- BCC
FROM
The From field indicates the sender’s address i.e. who sent the e-mail.
DATE
The Date field indicates the date when the e-mail was sent.
TO
The To field indicates the recipient’s address i.e. to whom the e-mail is sent.
SUBJECT
The Subject field indicates the purpose of e-mail. It should be precise and to the point.
CC
CC stands for Carbon copy. It includes those recipient addresses whom we want to keep informed but not exactly the intended recipient.
BCC
BCC stands for Black Carbon Copy. It is used when we do not want one or more of the recipients to know that someone else was copied on the message.
GREETING
Greeting is the opening of the actual message. Eg. Hi Sir or Hi Guys etc.
TEXT
It represents the actual content of the message.
SIGNATURE
This is the final part of an e-mail message. It includes Name of Sender, Address, and Contact Number.
Advantages
E-mail has prooved to be powerful and reliable medium of commmunication. Here are the benefits of E-mail:
- Reliable
- Convenience
- Speed
- Inexpensive
- Printable
- Global
- Generality
Reliable
Many of the mail systems notify the sender if e-mail message was undeliverable.
Convenience
There is no requirement of stationary and stamps. One does not have to go to post office. But all these things are not required for sending or receiving an mail.
Speed
E-mail is very fast. However, the speed also depends upon the underlying network.
Inexpensive
The cost of sending e-mail is very low.
Printable
It is easy to obtain a hardcopy of an e-mail. Also an electronic copy of an e-mail can also be saved for records.
Global
E-mail can be sent and received by a person sitting across the globe.
Generality
It is also possible to send graphics, programs and sounds with an e-mail.
Disadvantages
Apart from several benefits of E-mail, there also exists some disadvantages as discussed below:
- Forgery
- Overload
- Misdirection
- Junk
- No response
Forgery
E-mail doesn’t prevent from forgery, that is, someone impersonating the sender, since sender is usually not authenticated in any way.
Overload
Convenience of E-mail may result in a flood of mail.
Misdirection
It is possible that you may send e-mail to an unintended recipient.
Junk
Junk emails are undesirable and inappropriate emails. Junk emails are sometimes referred to as spam.
No Response
It may be frustrating when the recipient does not read the e-mail and respond on a regular basis.
Subscribe to:
Comments (Atom)